Tetrate Enterprise Gateway for Envoy

Seamlessly add Envoy Gateway to your stack
Are you using Kubernetes? Tetrate Enterprise Gateway for Envoy (TEG) is the easiest way to get started with Envoy Gateway for production use cases.
Get the power of Envoy Proxy in an easy-to-consume package managed by the Kubernetes Gateway API.
Developer Resources
TEG How-to Guides | TEG Developer Docs | Envoy Proxy Project
A lightweight gateway that meets your most critical needs
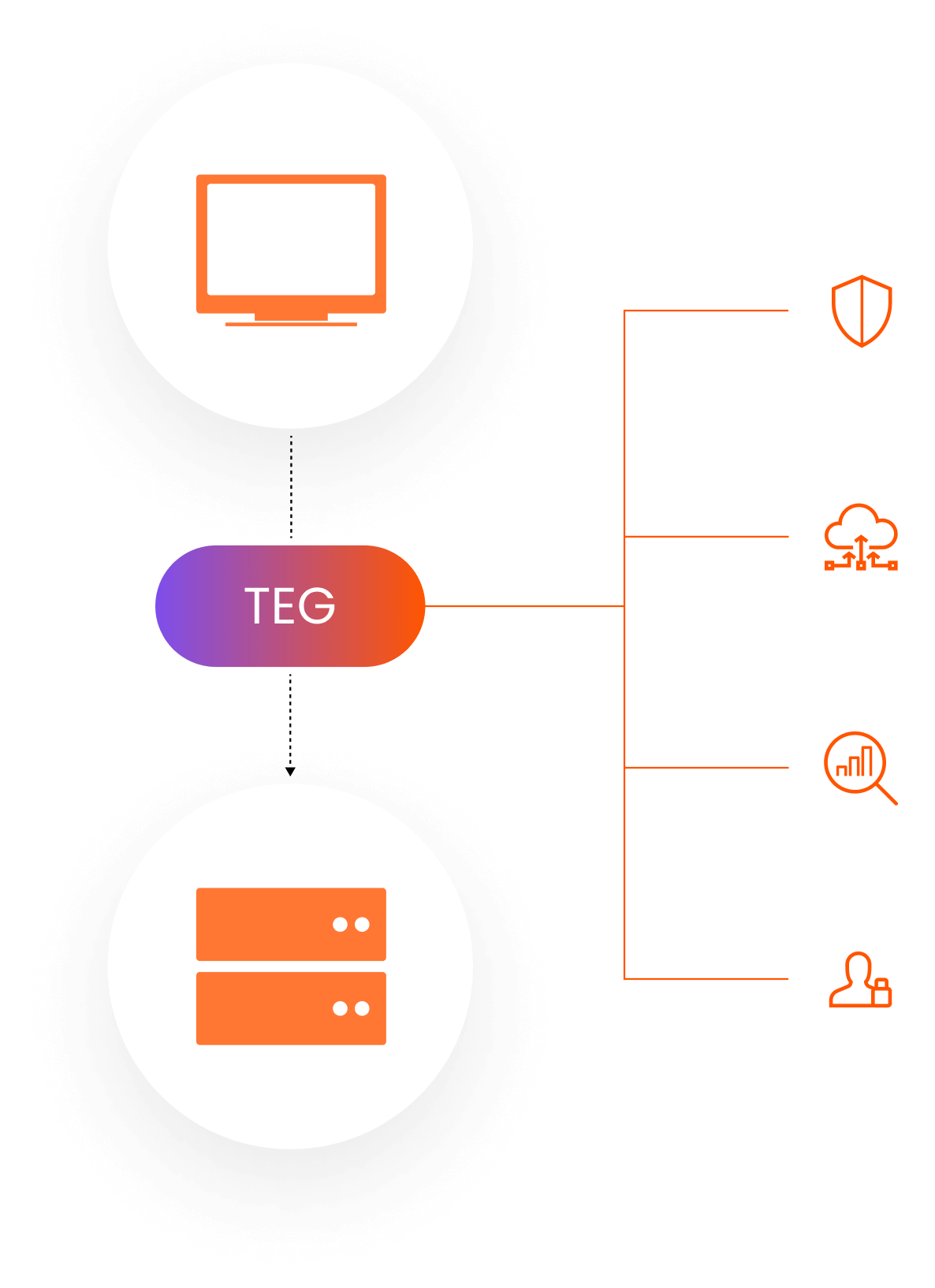

Protect your applications. Leverage WAF-based security at the ingress point to your cluster.
Manage application traffic. Rate limit traffic and make configuration based routing decisions, enabling canary released and failovers.
Observe traffic. Collect observability data in OTEL format and monitor traffic coming through the gateway.
Authenticate users. Integrate with OpenlD Connect providers to enable Single Sign On.
Schedule a demo or sign up to become a Tetrate developer partner today.
Built on Open Source for a Multi-Cloud World
Tetrate is a leading contributor to open source Envoy and Envoy Gateway. Tetrate Enterprise Envoy Gateway brings them to the enterprise, with the scale, reliability, performance and security necessary for large and mission-critical apps. Whatever your Kubernetes platforms of choice, rely on Tetrate’s expertise to deliver your services without missing a beat.
Why Tetrate Enterprise Envoy Gateway?
Envoy
Envoy Gateway
Tetrate Enterprise Gateway for Envoy