Cloud Native Service Gateway Is Here: Introducing Tetrate Enterprise Envoy Gateway
Today we are excited to announce that Tetrate Enterprise Envoy Gateway (TEG), the enterprise-ready distribution of Envoy Gateway is now available

Today we are excited to announce that Tetrate Enterprise Envoy Gateway (TEG), the enterprise-ready distribution of Envoy Gateway is now available! TEG is the cost-effective, modern standard service gateway for cloud-native infrastructure—we call it the cloud native API load balancer. You can get TEG directly on the AWS marketplace today.
Envoy Gateway, initiated by Tetrate with dozens of companies now contributing, is an exciting Envoy community open source project built to modernize Ingress in the cloud native landscape. Envoy Gateway significantly decreases the barrier to entry when using the Envoy Proxy for Ingress (sometimes referred to as “north-south”) use cases. It’s the first and best implementation of the Kubernetes Gateway API and provides the best idiomatic experience for deploying Envoy as your default Kubernetes ingress controller.
Tetrate Enterprise Envoy Gateway layers on top of pure OSS Envoy Gateway to support CVE and upgrade management for a smooth day two, FIPS-compliant builds for government environments, and a seamless experience using advanced Envoy features like global rate limiting and handling application authentication with OIDC and OAuth2. Finally, you have Tetrate’s world-class expertise and global team at your back to provide support when you need it.
If you want to get started right away, read the getting started blog, check out the docs, and sign up for a free evaluation copy. If you want to learn more about how Tetrate Enterprise Envoy Gateway works, read on.
Tetrate Enterprise Envoy Gateway Solves Common Kubernetes Adoption Challenges
We work closely with customers to understand how they are getting value from TEG. We’re already seeing repeated use cases and patterns. To name a few folks are using today:
High Performance, GitOps-Driven Application Ingress
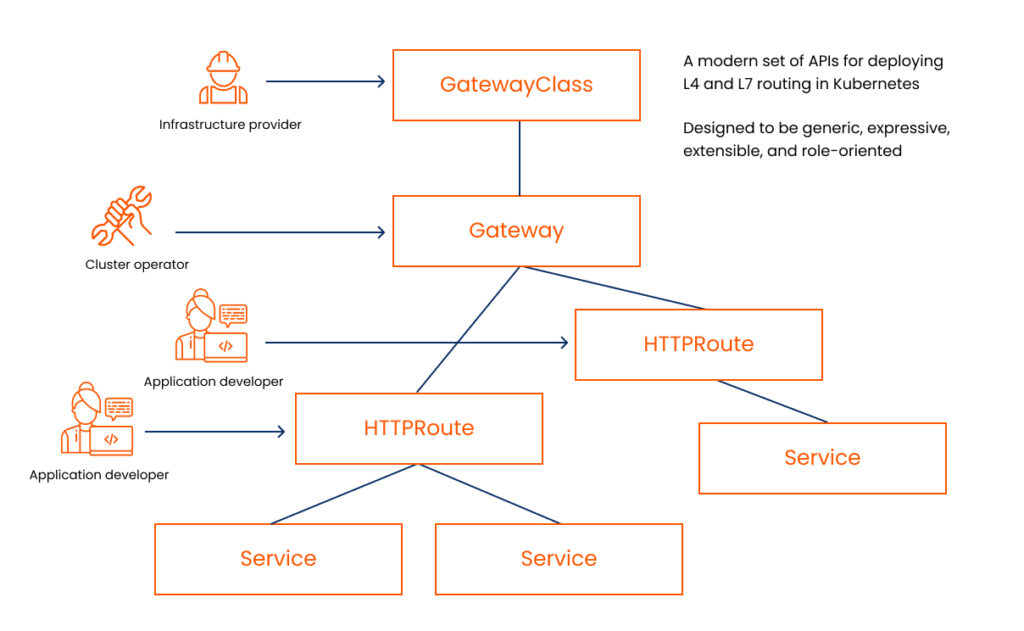
Envoy was designed from the ground up to be a highly performant edge and service proxy and is currently used by many organizations in the cloud native landscape. Through the Envoy gateway project, a control plane driven by the Kubernetes Gateway API takes care of managing configuration of the Envoy instances dynamically at runtime. The Kubernetes Gateway API, provides a more expressive next-generation alternative to the old Kubernetes Ingress API. It has been specifically designed to manage traffic from clients outside the cluster to services inside the cluster. By providing different object classes, the API is ideally suited to segment responsibilities between different teams and roles. As an example, it is possible to set up specific CI/CD pipelines for route management handled by application developers themselves, while providing cluster operators to manage their more deployment, resource, and security oriented configurations separately.

Authentication with OIDC and OAuth2
OpenID Connect is an interoperable authentication protocol based on the OAuth2 framework of specifications. As such it simplifies the way to verify the identity of users based on the authentication performed by an Authorization Server. Most organizations see the benefit of utilizing these technologies and plugging their favorite Identity Providers into their ecosystem. The biggest challenge however is protecting endpoints at the application level. Each service in your platform might be written in a different language or framework, and having all your application developers needing to thoroughly grasp and help maintain this layer is error prone, tedious, and distracts from focussing on your business logic. TEG provides an out of the box solution for managing your authentication concerns in a consistent and—above all—in a platform-wide manner. By integrating with your Identity Providers, TEG can protect all your APIs by enforcing the availability of an authenticated user and sending anonymous users to the correct location for identity verification.
Inbound Rate Limiting
Rate limiting blocks users, bots, or applications that are over-using or abusing API endpoints. With this capability they provide a critical measure to ensure application and platform resiliency. Setting up rate limit policies while scaling to multiple application ingress gateways is often not trivial. TEG provides out of the box support for global rate limiting, through a high performance rate limit middleware inside Envoy Gateway which can connect to a Redis server, cluster, or sentinel for budget synchronization. TEG therefore allows you to deploy a cluster of Ingress gateways protecting the same resources and managing their overall combined rate limit budgets.
Routing Outside Kubernetes
Within Kubernetes you get service discovery for free for services running inside the environment. Often organizations have mixed mode platforms where Kubernetes services coexist next to traditional VM applications, lambda functions, etc. TEG provides service discovery integration with systems like AWS Cloud Map and Hashicorp Consul allowing you to easily onboard and route to workloads outside of Kubernetes. This way you can leverage all the Ingress benefits of TEG while sending traffic to destinations not necessarily found in Kubernetes, making TEG a proper platform-wide ingress solution. This functionality also eliminates many pain points found when gradually migrating services to Kubernetes and helps you replace bloated legacy API Gateway solutions while navigating your cloud native strategy.
One of the areas we’re most excited about is integrating tightly with AWS Lattice to enable exposing and consuming services via Lattice endpoints as easily as services in Kubernetes. If you’re starting to use Lattice now, reach out – we’re looking for build partners!
Tiered Ingress
TEG enables you to keep consistent external addresses and consolidate policies for north-south traffic while allowing app-team self-serve on your infrastructure. Gone are the days of external load balancer change request processes taking multiple weeks just to allow application teams to make changes to their existing APIs or onboarding new ones. The TEG solution uses a Tier 1 Edge Envoy Gateway which takes care of concerns like TLS termination and auto-discovers clusters as they’re provisioned/deprovisioned. Per application, you can choose Active-Active or Active-Passive routing to the Tier 2 Application Envoy Gateways. The application gateways take care of routing the registered endpoints to the correct services, as set up and managed by the application teams themselves.
Cross-Cluster Ingress
Applications are often distributed across clusters in the same region for fault tolerance, however failing over between them per-application can be challenging. Since TEG automatically discovers other clusters and their available services based on configuration and rules, it can enable failover to remotes automatically as local traffic fails at a much faster pace then a Global Load Balancer (GLB) can respond. TEG helps to mitigate outages due to bad application rollouts and helps identify failures quickly with best in class visibility.
WAF with OWASP Core Rule Set
A Web Application Firewall (WAF) helps protect web applications by filtering and monitoring HTTP traffic between the applications and the internet. The OWASP Core Rule Set (CRS) is a set of generic attack detection rules for WAF implementations that aims to protect web applications from a wide range of attacks, including the famous OWASP Top Ten, with a minimum of false alerts. It provides protection against many common attack categories, including SQL Injection, Cross Site Scripting, Local File Inclusion, etc.Tetrate is a major contributor to the modern OWASP Coraza WAF ecosystem. Coraza provides a better alternative to ModSecurity which has announced end-of-life for support and maintenance. TEG will bundle the Coraza WAF with OWASP CRS in the next release.
What’s Next
The launch of Tetrate Enterprise Envoy Gateway marks a significant milestone in modernizing Kubernetes Ingress. As we’ve discussed here, TEG not only simplifies and streamlines the deployment of Envoy Proxy for Ingress but also addresses common challenges faced in Kubernetes adoption.
To get started with TEG right away, check out the documentation and sign up for a free trial.










