Tetrate Service Express technical preview now available in Amazon EKS
Tetrate Service Express technical preview now available. You can sign-up now to get access to the technical preview. You will get early access to upda

Tetrate Service Express technical preview now available.
You can sign-up now to get access to the technical preview. You will get early access to updates, documentation, and collaboration with our product team to provide feedback.
We are excited to announce Tetrate Service Express, a service connectivity, security and resilience automation solution for Amazon EKS. We built Tetrate Service Express on open source service mesh components such as Istio and Envoy and optimized it for easy installation, configuration and operation on AWS. If your team is experimenting with service mesh on AWS and you need to quickly prove the ROI without mastering complex Istio and AWS primitives, then try Tetrate Service Express. If your team already has a service mesh on a single cluster, but want to extend your mesh to multiple clusters or even regions, Tetrate Service Express can help also.
For the impatient, watch a quick 3-minute demo below, and get on the waitlist for your evaluation copy today.
If you want to get a deeper overview of Tetrate Service Express’s new features, read on.
Why Tetrate Service Express
If your organization wants to create a better customer experience, improve operational efficiency, or protect intellectual property, chances are it must build and run software—higher quality, faster releases, better uptime. And most likely, app dev teams, operations teams and platform teams are pursuing these objectives with the aid of two innovative trends: the flexibility of cloud infrastructure and microservices.
Many teams are opting for the convenience of Amazon EKS as they build microservices in the cloud. However, as they scale EKS workloads they find themselves asking questions such as:
- How do I secure microservice components distributed across AWS?
- How do I maintain reliability when individual components fail during updates or under load?
- How do I manage traffic to, from, and between services when everything is dynamic and manual configuration no longer works?
Increasingly, a Platform Operations team will create a dedicated infrastructure layer on top of microservices—a service mesh—that provides service discovery, security, authentication, and observability across the microservice components. Istio and Envoy are open source standards for the service mesh control and data plane, but Istio and Envoy are only partial solutions because they add new operational complexities for teams running Amazon EKS.
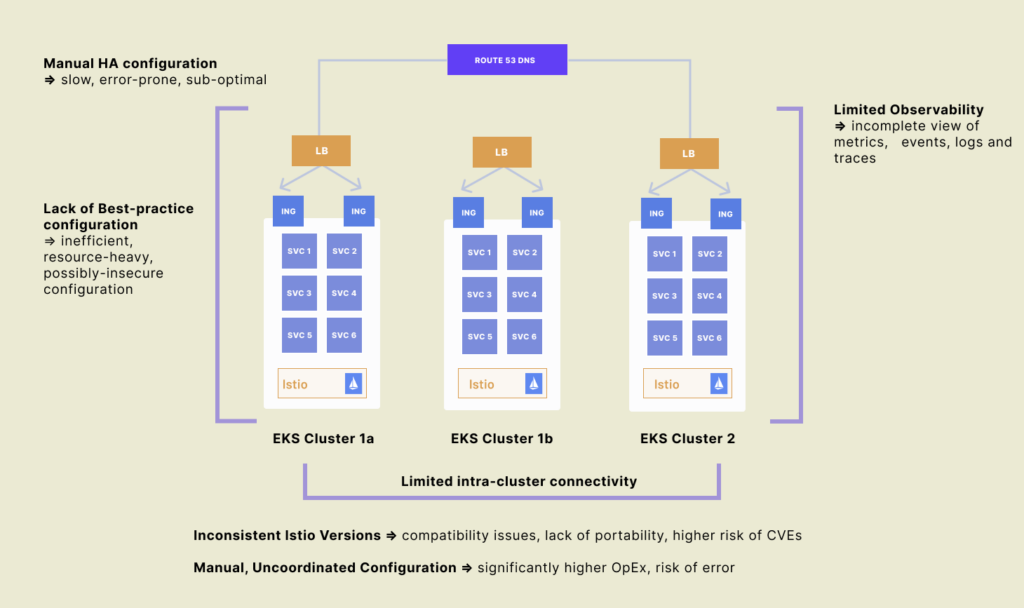

Tetrate Service Express provides service mesh automation for the Platform team on top of Istio and Envoy. It handles the installation and configuration of open source components on Amazon EKS, integrates with AWS services and provides a management console for platform operators to configure the service mesh for security, resilience, and observability faster.
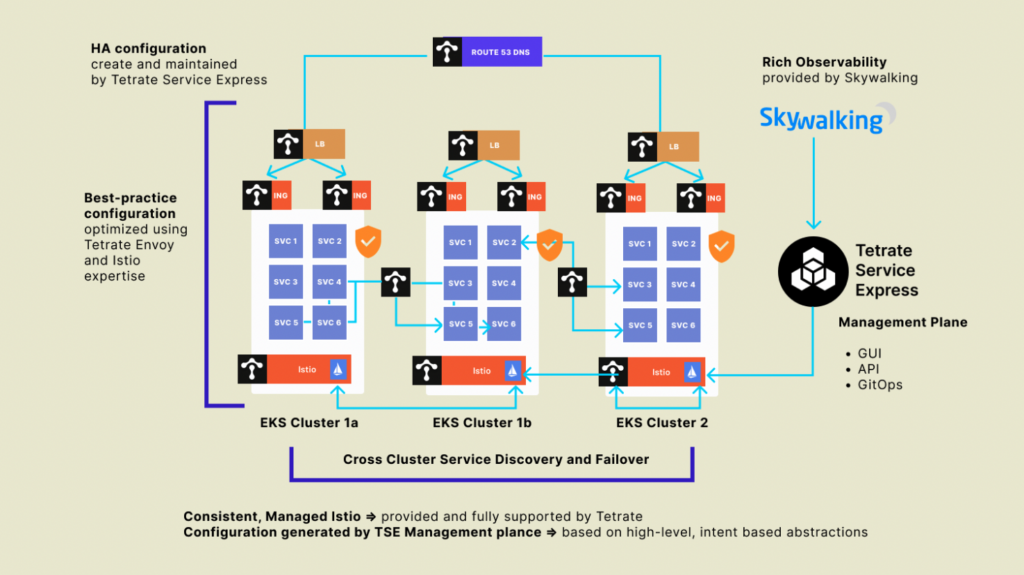

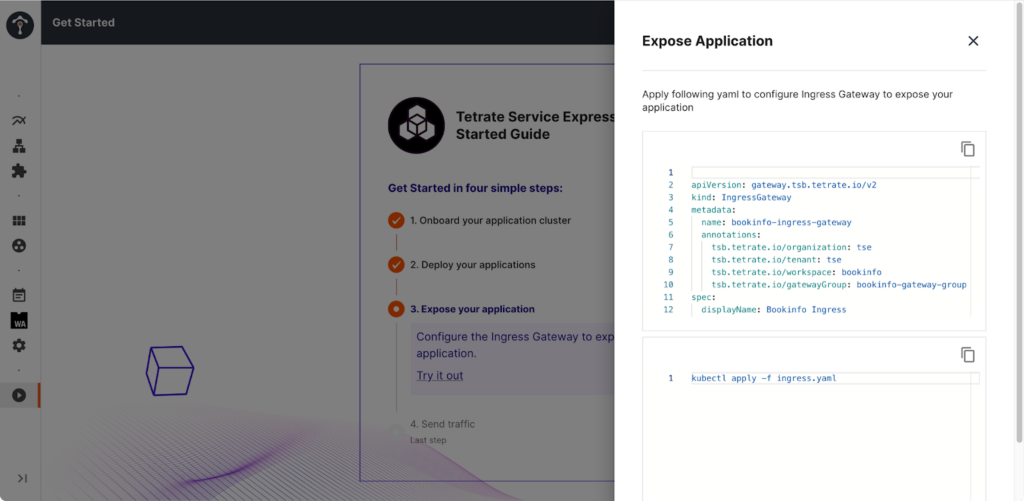
Fast installation on Amazon EKS and integration with AWS services
Getting Istio up and running on EKS might be becoming easier (for example with the Tetrate Istio Distro EKS add-on), but a lot more needs to be done before you can operate a functional service mesh:
- How do I ensure all service mesh components are installed and configured correctly?
- How do I define the network infrastructure around Istio and Envoy to enable secure, cross-cluster connectivity and availability?
- How do I observe and troubleshoot services on the mesh to assist in scaling and optimization?
TSE can be installed easily with helm charts on EKS, and integrates easily with Route 53 and NLB (or other AWS load balancer types) so that you can quickly:
- Position edge and ingress gateways for your services to manage and secure the entry points, ingress, and egress traffic.
- Deliver APIs from your applications with authentication, rate limiting, HA and security built-in.
- Obtain MELT (Metrics, Events, Logs, Traces) for your services and apps.

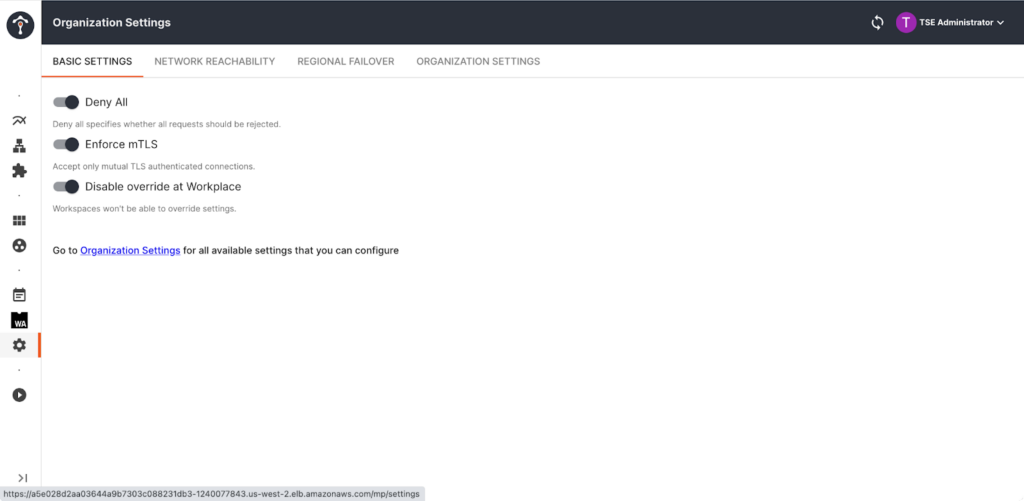
One-step encryption between services with mTLS
One of the first use cases of a service mesh is to enable inter-service encryption with mTLS, but things get complicated quickly once you expand beyond a single cluster:
- How can I establish and manage a single root-of-trust across clusters?
- How do I enforce mTLS everywhere, to support a zero-trust posture?
- How can I rotate my certificates regularly, and respond in the event of a leaked or compromised cert?
Tetrate Service Express makes it easy to encrypt services and apply a zero-trust posture by providing:
- A built-in, easy-to-use certificate authority that rotates and manages certificates across all of your clusters.
- The ability to define, at an administrative level, the need for mTLS for all services.
- The ability to create fine-grained access policies, beginning with a Deny-All posture by default.

Easy failover set up between clusters and regions
As you define your application infrastructure, one of the more complicated things to set up is internal HA of your services, especially across regions. Some of the complication you might encounter include:
- How do I configure Route53, Amazon Load Balancing and other load balancing services to achieve reliable HA across different clusters?
- How do I set up cross-cluster communications and internal high-availability without hairpinning?
- How do I automate network configuration changes when a service fails?
Tetrate Service Express makes achieving service HA easy by providing:
- Automatic configuration of ingress, Amazon load balancing and Route 53 for service publishing.
- Automatic configuration of internal and east / west gateways for internal high availability.
- Dynamic reconfiguration of networking rules to fail traffic over across and between clusters with minimal interruption in service.

What’s next
Now in Technical Preview, sign-up now to access the evaluation software, access to a new docs portal, and a slack community channel.










