Many apps in one Kubernetes Cluster? Consider a dedicated Gateway per app
In the previous blog post, I introduced how Istio manages certificates, and in this article, I will guide you on how to use an external certificate au

Managing ingress traffic configurations in Kubernetes can be challenging, especially when each application has different requirements. If you’re using a single shared Gateway across all your namespaces, you may be sacrificing and creating more complexity rather than simplicity.
Using a dedicated Gateway per namespace can provide more control and better isolation. It enables each application team to manage its own Gateway without trying to figure out how all the configs can work together across teams.
Let’s look at how a dedicated Gateway per namespace can help streamline ingress traffic handling in a multi-tenant Kubernetes cluster.
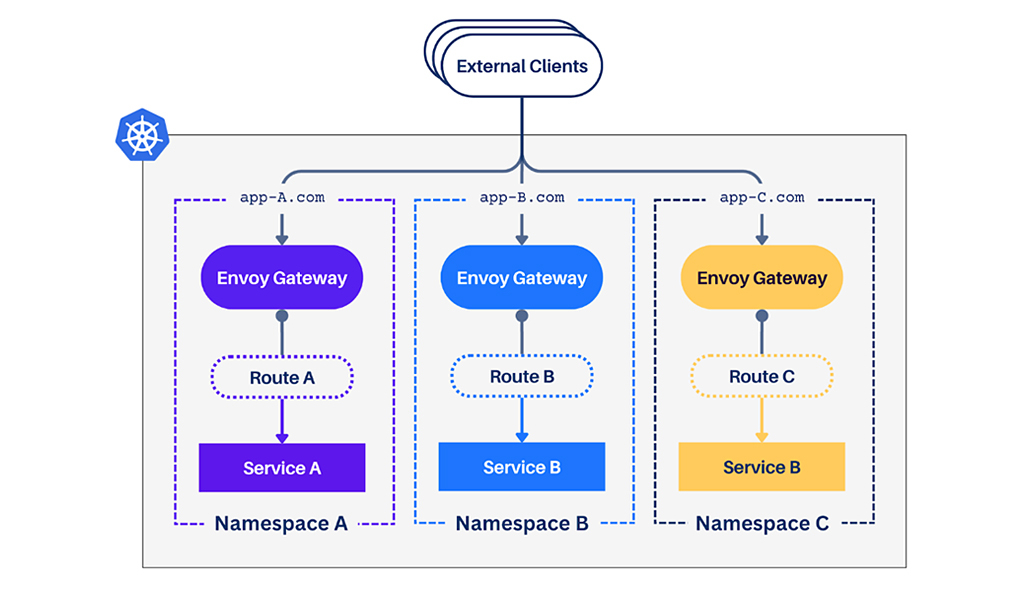

Why Choose a Dedicated Gateway Per Namespace?
Teams may want to control how traffic enters their sub-system in a multi-team, multi-app environment.
A dedicated Gateway per namespace offers:
- Application-Specific Policies: Customize traffic policies such as rate-limiting, mTLS, or authentication per app without impacting other apps.
- Isolation and Security: Isolate ingress traffic for each app, providing boundaries between teams or services. With a dedicated Gateway per app, you can create OIDC integrations based on the app at the Gateway level.
- Granular Control: Application teams can independently manage and update their Gateway configuration without concern about how a policy applied at the Gateway may impact all apps.
Tetrate offers an enterprise-ready, 100% upstream distribution of Istio, Tetrate Istio Subscription (TIS). TIS is the easiest way to get started with Istio for production use cases. TIS+, a hosted Day 2 operations solution for Istio, adds a global service registry, unified Istio metrics dashboard, and self-service troubleshooting.
What Is a Dedicated Gateway Per Namespace?
A Dedicated Gateway per namespace is an architecture where each namespace has its own Gateway instance. This model gives each app or team full control over managing traffic for their specific namespace.
Instead of sharing a single entry point, each app has its own Gateway, with separate routing, security, and traffic management configurations. This separation ensures that changes in one namespace don’t accidentally affect traffic management for another.
Envoy Gateway, an implementation of the Kubernetes Gateway API, extends these capabilities by providing powerful features like advanced traffic routing, load balancing, and built-in observability.
Is a Dedicated Gateway Right for Your Kubernetes Setup?
A dedicated Gateway per namespace is a great fit if:
- Multiple teams are sharing a Kubernetes cluster and need independence in traffic configuration.
- Traffic isolation between different applications or services is helpful when you want to fail over a single app to another region and not the whole cluster.
- You want to avoid a “one size fits all” approach to traffic management and routing policies.
If this resonates with your architecture needs, a dedicated Gateway might be your right choice.
Ready to Get Started?
You can implement app-dedicated gateways without reworking your Kubernetes setup. Start by installing the latest Gateway API, which can be done without upgrading your Kubernetes version.
Then, deploy Envoy Gateway to manage the traffic in your cluster. As your architecture grows, you can add more advanced features like rate-limiting, load balancing, authentication, and custom routing logic.
Check out this guide to get started with Envoy Gateway. The helm chart will install the necessary Gateway API resources.
Let’s Talk
Are you curious about how a Shared Gateway architecture can optimize traffic management in your Kubernetes environment? Contact us to explore how we can help you design and deploy an efficient, scalable solution for your platform.










