DevSecOps, Service Mesh, and Zero Trust Architecture: A Recap of the 2021 NIST-Tetrate Conference
Tetrate and NIST co-hosted our second annual conference last week focusing on foundational approaches to security in the era of microservices

Tetrate and NIST co-hosted our second annual conference last week focusing on foundational approaches to security in the era of microservices: DevSecOps and Zero Trust Architecture in Multi-Cloud Environments. The one-day event took place virtually on Jan. 27, 2021. Here are some highlights!
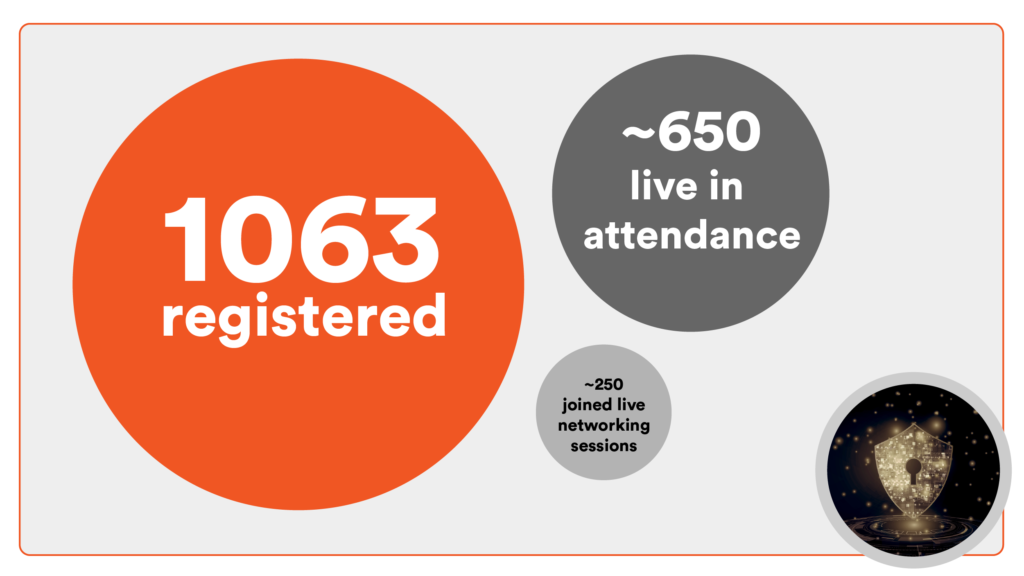
In attendance: by the numbers
With more than 1,000 people registered, we had a robust audience representing a diverse swath of both enterprise and governmental agencies. Groups of 40-80 attended each of the networking breakout rooms at lunch on zero trust, DevSecOps, service mesh, and multi-cloud. Thanks to the audience, thoughtful questions asked in the main session chat and in the lunch breakout rooms kept the conference rich and lively.

Speakers and sessions
The conference kicked off with a keynote from Tetrate CEO Varun Talwar, followed by sessions featuring NIST scientists and IT leaders from the U.S. Air Force, Departments of Commerce (DoC) and Homeland Security (DHS), and the Food & Drug Administration (FDA), as well as cybersecurity experts and engineers from RSA, Flexport, the University of Maryland and Tetrate.


The full recording is posted here and divided into four sessions:
Session 1
- Varun Talwar opened the conversation framing service mesh, “zero trust” and DevSecOps as necessary, foundational approaches to security today, noting that API abuses will be the most frequent attack vector by 2022.
- Dr. Ronald Ross, NIST Fellow, presented on the imperative to reduce and manage complexity in cybersecurity that is no longer served by the paradigm of the perimeter.
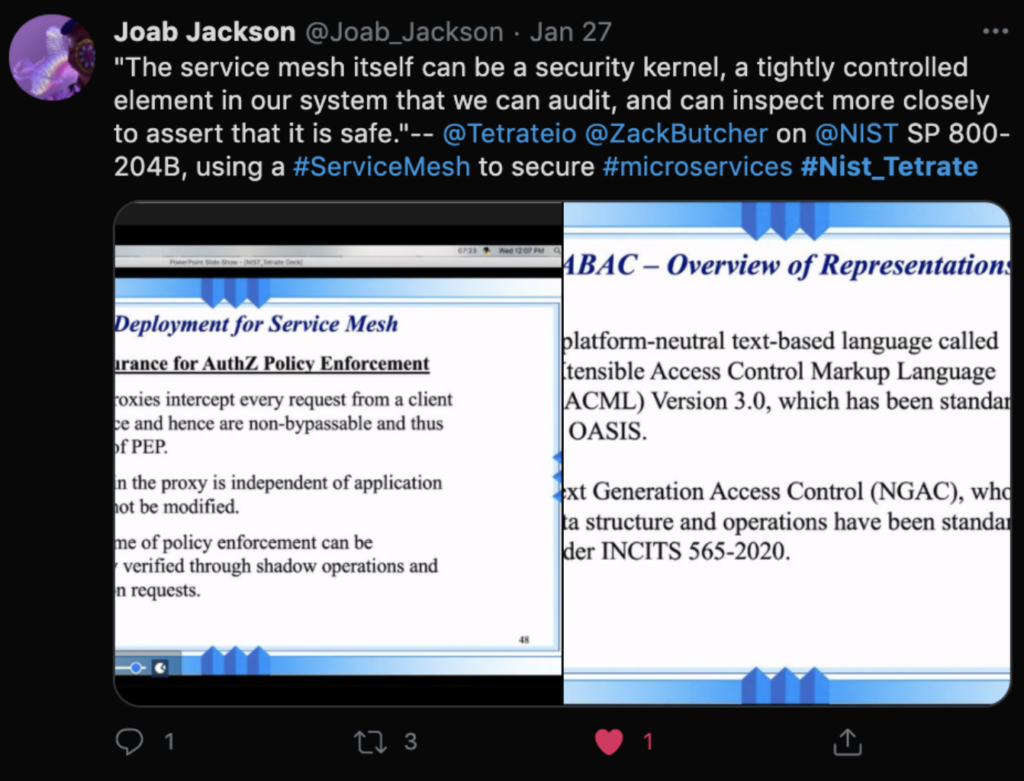
- And Zack Butcher from Tetrate and Ramaswamy Chandramouli from NIST presented on the just-released draft of their NIST special publication on ABAC and Next Generation Access Control (NGAC) used in a service mesh– an internal implementation guideline for federal projects.
“Instead of providing piecemeal security solutions for each of the components, we have this wonderful concept called a service mesh.” –Ramaswamy Chandramouli

Session 2:
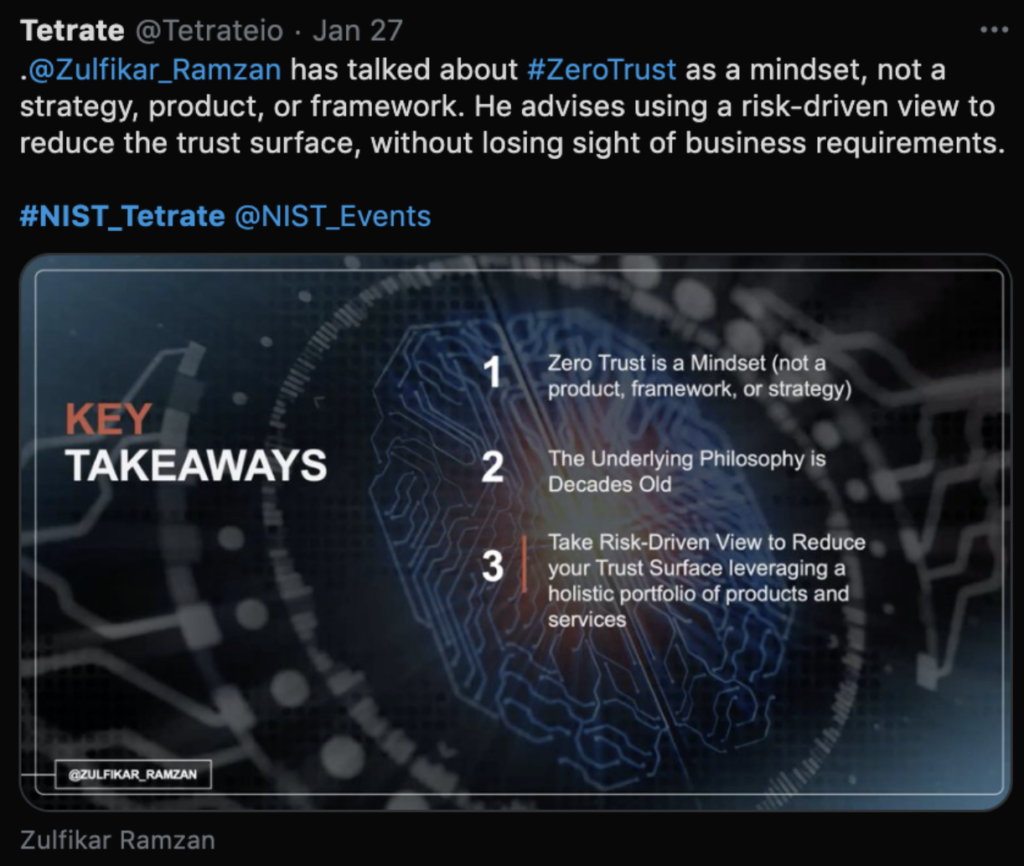
- Dr. Zulfikar Ramzan, CTO of RSA, spoke on the history and future of “zero trust,” describing it as a “mindset” whose foundational concepts are secure access, strict (“need-to-know basis”) access control, and traffic monitoring.

- Nicolas Chaillan, Chief Software Officer for the Air Force and co-lead of the Department of Defense Enterprise DevSecOps initiative, described how Platform One has implemented DevSecOps standards and tools like Istio service mesh that bake in layers of preemptive security to thwart attacks and to “ensure mission-critical applications are deployed with secure, resilient miniservices and microservices operations.”
- Tetrate’s Adam Zwickey described how the benefits of having a DevSecOps “assembly line” model accrue to potentially hundreds of developers and hundreds or thousands of services across an enterprise.
## Session 3:“If you’re not using a service mesh, you’re probably not going to be able to move at the pace of relevance.” –Nicolas Chaillan
- Ignasi Barrera of Tetrate and Joshua Roberts from NIST opened the afternoon session with live demos: Barrera demonstrated identity provisioning in a service mesh, and Roberts demonstrated the use of next generation data access control for federated sharing of database resources

- Andrew Weiss, Lead Architect and Technical Advisor, UMBC, led a session on “Blockchain-based Secure Software Assets Management (BloSS@M).
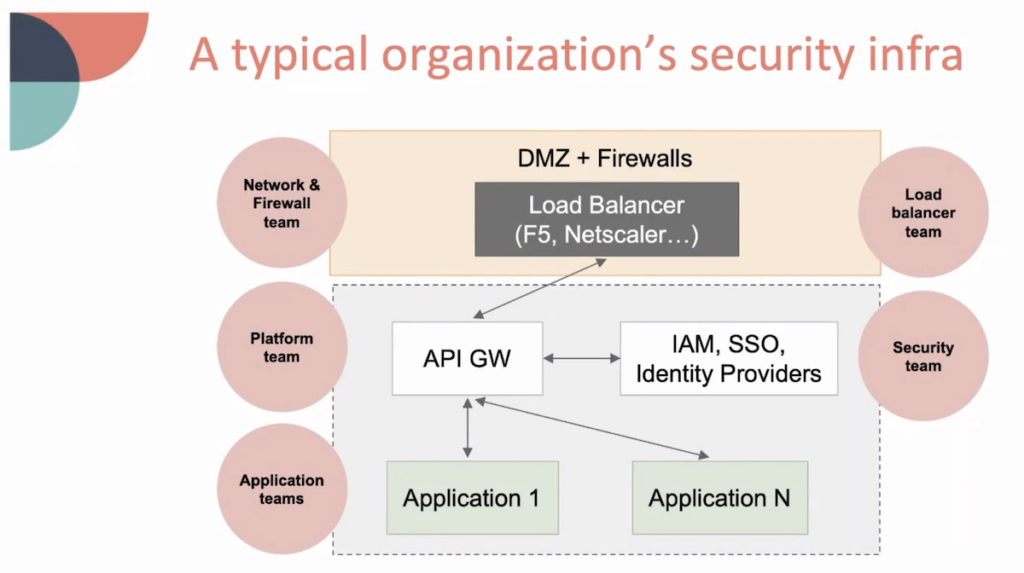
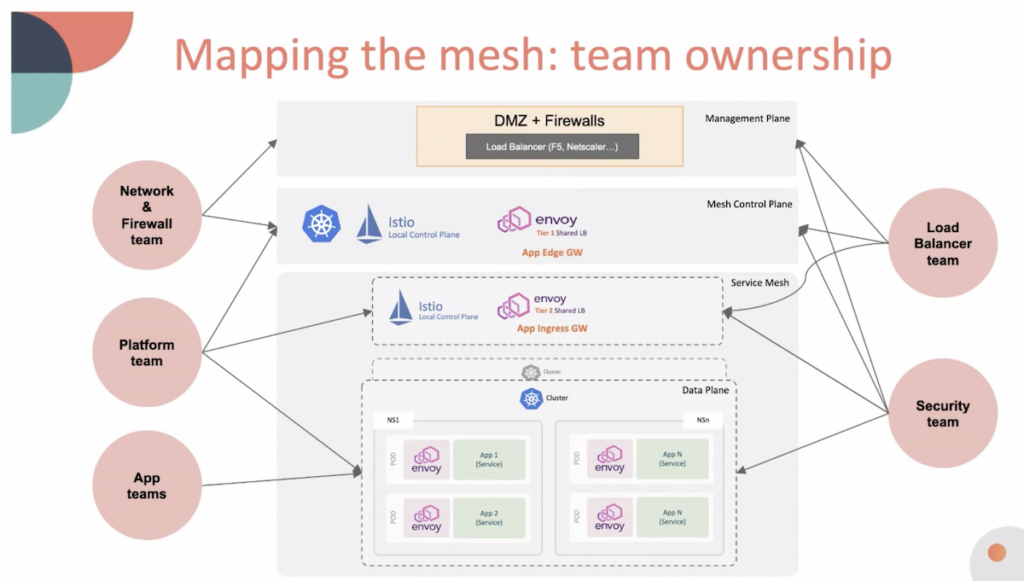
Kevin Paige of Flexport, who is preparing to use Istio in production, spoke on the “transition to service mesh,” outlining how teams in an organization map onto a traditional security infrastructure vs. a mesh architecture.


Session 4:
The final session was a “fireside chat” panel session with thought leaders Chaillan, Butcher, André Mendes (DoC), Dr. Sorin Nastea (FDA), and James Younger (DHS), moderated by NIST’s Dr. Michaela Iorga.
What’s next:
- To read more, Tetrate offers a complimentary white paper on zero trust.
- Tetrate and NIST have collaborated to implement NIST’s Next Generation Access Control standard; contact Tetrate to learn more.
- Share your takeaways on Twitter #NIST_Tetrate
- Slide decks from the presenters will be shared once available.
- Tetrate Service Bridge helps deliver zero trust architecture with authentication, dynamic authorization, encryption, service discovery, request routing, load balancing, self-healing recovery, and service instrumentation. It implements NIST’s Next Generation Access Control standard; contact Tetrate to learn more.










