Accelerate Zero Trust Adoption with CISA’s Zero Trust Maturity Model 2.0
In today’s landscape of increasingly frequent and sophisticated cybersecurity threats, federal agencies require a new security model that can effectiv

In today’s landscape of increasingly frequent and sophisticated cybersecurity threats, federal agencies require a new security model that can effectively adapt to the complexity of the modern environment, embrace the hybrid workplace and safeguards people, devices, apps and data, wherever they’re located.
To address this need and provide guidance for organizations striving to enhance their cyber resilience, the Cybersecurity and Infrastructure Security Agency (CISA) released an update to the Zero Trust Maturity Model (ZTMM). ZTMM 2.0 builds upon the initial version released in September 2021, to assist organizations in implementing Zero Trust policies into their daily operations and overarching security strategies. Automation and dynamic processes are critical aspects highlighted throughout the ZTMM 2.0 document. At every stage of maturity, automated processes and systems are cited as essential criteria for achieving maturity goals. Another key theme within ZTMM 2.0 is the integration of various pillars. From the initial maturity stage, the model stresses the need for cross-pillar integration, emphasizing the interconnectedness of different aspects of Zero Trust implementation. CISA suggests that federal agencies anticipate a substantial increase in effort and realized benefits as Zero Trust maturity progresses across and within the pillars of the framework. By providing a clear roadmap and emphasizing automation and integration, ZTMM 2.0 empowers federal agencies and organizations across all industries, to advance their security posture and embrace the principles of Zero Trust.
By incorporating these updates, CISA’s Zero Trust Maturity Model offers a comprehensive framework that supports organizations in their pursuit of a robust Zero Trust architecture (ZTA). It encourages a step-by-step approach, allowing organizations to make incremental advancements and adapt their strategies according to their specific needs and existing infrastructure. While the ZTMM is specifically tailored for federal agencies, businesses in all verticals can benefit from these recommendations on their Zero Trust journey. ZTMM 2.0 introduces a new stage called “Initial” that can be used as a guide to identify maturity toward each pillar. In all four stages of maturity (Traditional, Initial, Advanced, Optimal) CISA has also added several new functions and updated existing functions to consider when organizations plan and make decisions for ZTA implementation.
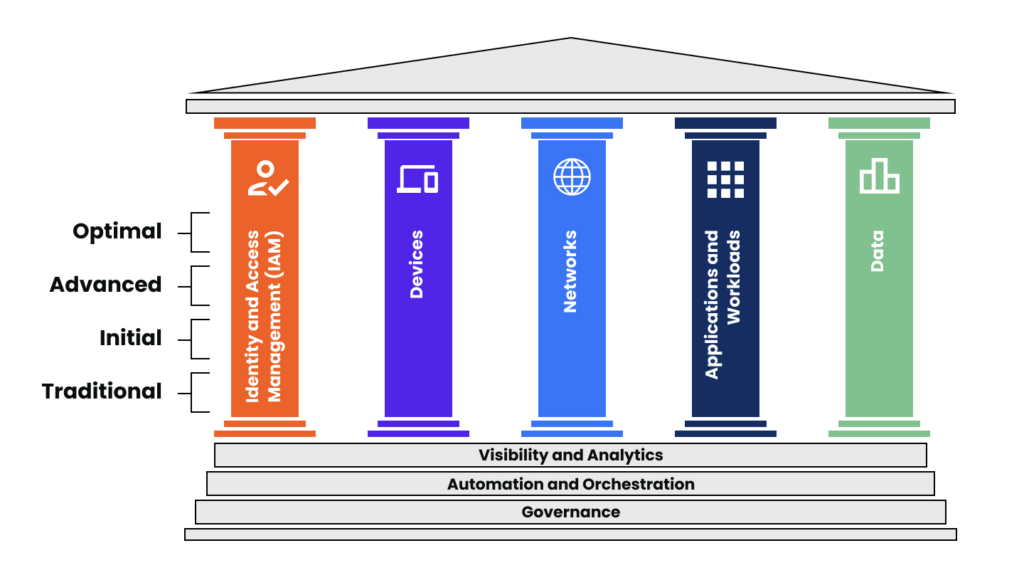

CISA has outlined the following five pillars as part of its Zero Trust Maturity Model: Identity, Devices, Networks, Applications and Workloads and Data.
- Identity and Access Management (IAM): This pillar focuses on establishing strong identity and access controls. It involved implementing multi-factor authentication (MFA), strong password policies and user identity verification mechanisms. IAM also includes user provisioning and deprovisioning processes to ensure access privileges are granted and revoked appropriately.
- Devices: This pillar emphasizes securing devices that access an organization’s resources. It involves implementing measures such as device inventory and asset management, secure configuration baselines, continuous monitoring, and threat protection mechanisms. Device security also includes techniques like network segmentation and enforcing policies based on device health and compliance.
- Networks: This pillar focuses on securing network traffic and connections within an organization’s environment. It involved techniques such as micro-segmentation, network zoning and the use of virtual private networks VPN). Network security also encompasses network monitoring, intrusion detection and prevention systems and the use of encryption technologies to protect data in transit.
- Applications and Workloads: This pillar focuses on the systems and applications being executed on as well as remotely, such as in cloud environments. The process analyzes how applications are accessed, security measures that protect applications and the presence of threat identification and mitigation measures.
- Data: This pillar centers around protecting sensitive data throughout its lifecycle. It involves encryption mechanisms, data classification and labeling, data loss prevention (DLP) measures and data access controls. Data security also encompasses techniques such as data discovery, data masking and ensuring secure data storage and backups.
These five pillars of CISA’s Zero Trust Maturity Model provide a comprehensive framework for organizations to assess and improve their Zero Trust security posture. By addressing each pillar, organizations can establish a strong foundation for implementing Zero Trust principles and enhancing their overall cybersecurity resilience.
Zero Trust Maturity Stages
Zero Trust is a shift from a location-centric model to a more data-centric approach that aligns with the new reality of a widely distributed, hybrid workforce. Moving to a Zero Trust architecture is more than a technical challenge, it also is a cultural shift in cybersecurity policy. Understanding that the transition to a Zero Trust environment will take time and investment, the ZTMM recommends a four-stage approach :
- Traditional security architecture – manually configured lifecycles (i.e., from establishment to decommissioning) and assignments of attributes (security and logging); static security policies and solutions that address one pillar at a time with discrete dependencies on external systems; least privilege established only at provisioning; siloed pillars of policy enforcement; manual response and mitigation deployment; and limited correlation of dependencies, logs, and telemetry.
- Initial Zero Trust architecture – starting automation of attribute assignment and configuration of lifecycles, policy decisions and enforcement, and initial cross-pillar solutions with integration of external systems; some responsive changes to least privilege after provisioning; and aggregated visibility for internal systems.
- Advanced Zero Trust architecture – wherever applicable, automated controls for lifecycle and assignment of configurations and policies with cross-pillar coordination; centralized visibility and identity control; policy enforcement integrated across pillars; response to pre-defined mitigations; changes to least privilege based on risk and posture assessments; and building toward enterprise-wide awareness (including externally hosted resources).
- Optimal Zero Trust architecture – fully automated, just-in-time lifecycles and assignments of attributes to assets and resources that self-report with dynamic policies based on automated/observed triggers; dynamic least privilege access (just-enough and within thresholds) for assets and their respective dependencies enterprise-wide; cross-pillar interoperability with continuous monitoring; and centralized visibility with comprehensive situational awareness.
Moving the U.S. Government Toward Zero Trust Cybersecurity Principles
The move to Zero Trust will take time, but efforts can be accelerated with the right tools. Tetrate is committed to helping federal agencies and enterprises implement Zero Trust architecture effectively. Our Application Networking and Security platform helps organizations adhere to CISA’s ZTMM by enhancing identity and access controls, securing device communications, enforcing network security policies, protecting data and providing visibility for monitoring and analysis. Download Tetrate’s Zero Trust solution brief for more details.
If you’re interested in learning more about how Tetrate can help your organization achieve the ideal level of Zero Trust maturity, contact us today.










