Why Tetrate
Power Next-gen Networking And Security With An Istio-Based Service Mesh
Today, organizations cannot continue to rely on legacy network architectures. As applications evolve into collections of decentralized microservices, monitoring and managing the network communications and security among those myriad services becomes challenging.
Tetrate is the answer to the challenges of modern application networking and security. We deliver the world’s leading Application Networking and Security Platform built on top of open source Istio and Envoy with a modern management plane that brings centralized governance and decentralized enforcement of application networking – essential for implementing Zero Trust security across legacy and modern workloads.
Zero Trust addresses the following key principles based on the NIST guidelines:
Connect & Protect
Tetrate provides a consistent way to connect and protect thousands of individual microservices and deliver Zero Trust security operations across any environment. Security operators can easily implement service-to-service security including encryption, role-based access and authentication across services.
Simplify Traffic Management
Intercepting network traffic empowers the service mesh to manage it. Tetrate’s service mesh provides various kinds of traffic management that meet different demands including: traffic routing, traffic splitting, canary deployments and traffic monitoring.
Improve Visibility & Troubleshooting
Tetrate’s service mesh provides observability into the health and performance of your services to streamline and simplify troubleshooting. Reduce mean time to identify (MTTI) to maintain the highest service-level agreements (SLAs) and optimal application performance.
Ensure Compliance
Protect the rapidly growing number of services, APIs and data across the enterprise and ensure regulatory compliance especially in critical environments under regulatory regimes like PCI, HIPAA, GDPR and FIPS/FedRamp.
Open Source And Enterprise-Ready
We are the co-creators of open source Istio and Envoy – the leading open source service mesh and proxy, with millions of downloads and a thriving community of contributors.
We’ve worked within the open source Istio and Envoy projects as co-founders and as leading contributors to develop an understanding of the best coud-native practices, tools and integrations to support enterprise adoption of the service mesh.

Inside Envoy, The Proxy for the Future – a documentary that delves into the origins and rapid ascent of one of the most significant open source projects in the community today, featuring Tetrate co-Founder Varun Talwar
Setting The Standards For Zero Trust
Security in the cloud is being recast from static and IP-based, defined by a perimeter – to dynamic and identity-based, with no clear perimeter. This concept is known as Zero Trust. A service mesh is a modern and powerful tool to implement a Zero Trust architecture enterprise-wide.
Tetrate partners with the National Institute of Standards and Technology (NIST) to define and promote the standards for Zero Trust security. Using NIST’s experience with cybersecurity and Tetrate’s expertise on secure service mesh, we have collaborated to produce U.S. security standards for a distributed architecture:
- (SP 800-204A) Building Secure Microservices-based Applications Using Service-Mesh Architecture
- (SP 800-204B) Attribute-based Access Control for Microservices-based Applications using a Service Mesh
- (SP 800-204C) Implementation of DevSecOps for a Microservices-based Application with Service Mesh
- (SP 800-207A) A Zero Trust Architecture (ZTA) Model for Access Control in Cloud-Native Applications in Multi-Location Environments
- Implementation of next generation access control (NGAC), a superior authorization framework that’s more fine-grained than role-based access control (RBAC) and attribute-based access control (ABAC), in Tetrate’s products
Unite Developer, Platform And Security Teams
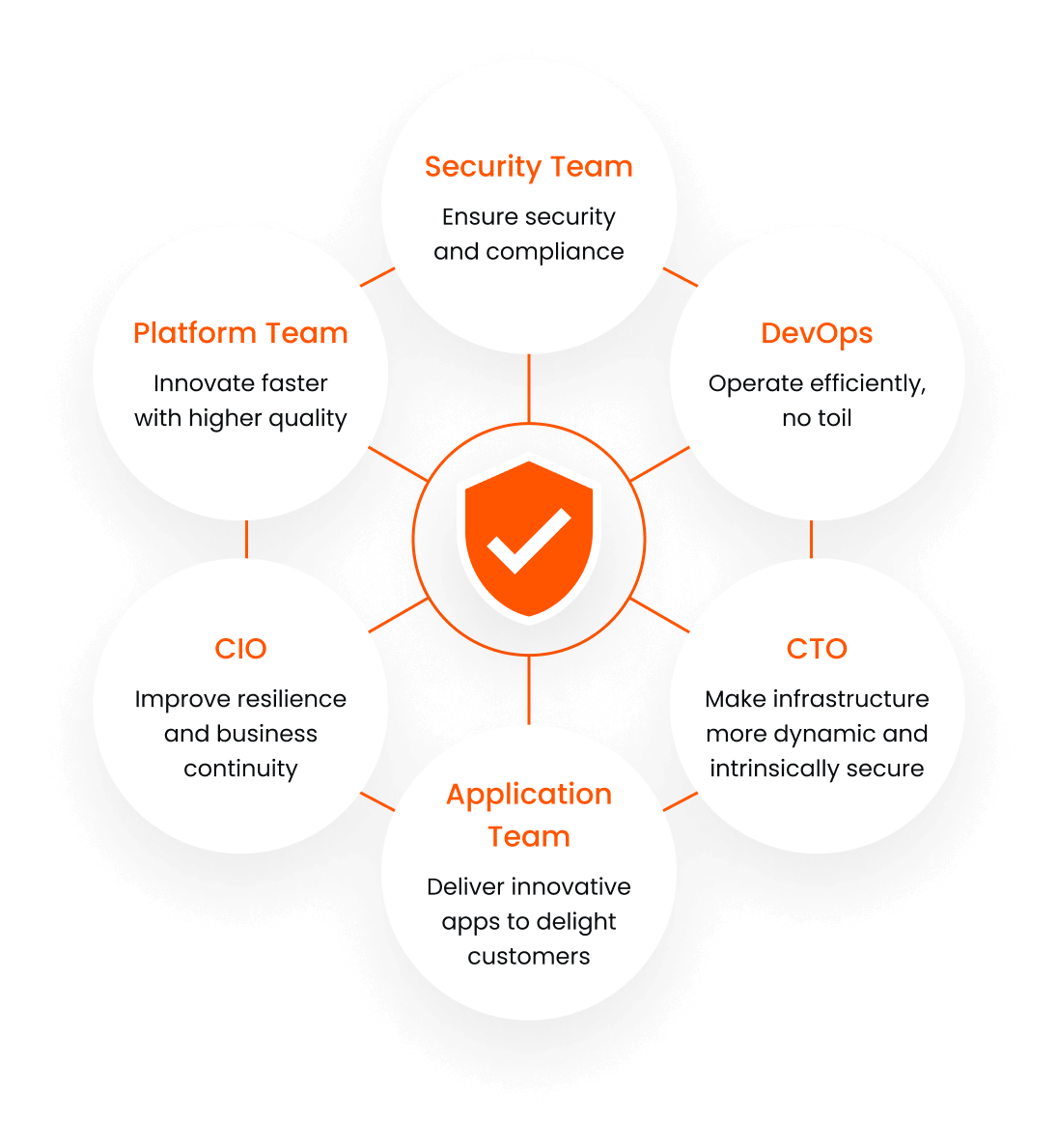
Tetrate’s service mesh offers a seamless operational model that supports Shift Left practices and promotes collaboration between Developer, Platform and Security teams to drive global DevOps and security strategies.
Trusted By Innovators, Big And Small
We’ve been working with organizations large and small around the world for years to help them adopt the service mesh and run it in production. Hundreds of innovative companies from startups to Fortune 500s use Tetrate to accelerate application modernization and implement a foundation of Zero Trust security.
Additional Resources
Take the Next Step
Learn how we can help you scale service mesh success across your enterprise.