Tetrate Recognized in Gartner’s Hype Cycle for Zero Trust Networking, 2023
Tetrate’s mention in this influential document reaffirms our expertise and innovative contributions to the Zero Trust networking landscape, particular

Tetrate’s mention in this influential document reaffirms our expertise and innovative contributions to the Zero Trust networking landscape, particularly in the realm of service connectivity and security. We believe our inclusion is a recognition of our:
- Collaboration with the National Institute of Standards (NIST) to establish Zero Trust guidelines
- Industry-leading application networking and security platform built on open source Istio and Envoy
- First FIPS-compliant Istio distro
- Team of experts ready to help you on your Zero Trust journey.
Zero Trust Adoption Accelerates
In the report, Gartner predicts that by 2026 10% of large enterprises (i.e., have over $1 billion annual revenue and/or more than 1,000 employees) will have a comprehensive, mature and measurable Zero Trust program in place, a significant rise from less than 1% in 2023.
Implementing a Zero Trust security framework is a best practice to establish a cybersecurity culture, especially in the cloud. The goal of Zero Trust is continuous protection across all attack surfaces. Those surfaces include all physical assets in the network, data center, cloud and at the endpoints, as well as networked software, data and the users themselves.
As Gartner recognizes, organizations are increasingly adopting Zero Trust because it can handle the security needs of today’s hyper-connected, hybrid networks—and this hyperconnectivity means that a single compromise can test the cyber resilience of the entire organization. “Zero trust is shaping the architectural approach for many organizations in the wake of government guidance and the constant onslaught and effectiveness of attacks. Zero trust is built upon a foundation of strong and unified identity and is supported by several technologies identified in this Hype Cycle, including the service connectivity layer, zero trust network access (ZTNA) and microsegmentation.” says Gartner.
A foundational layer of any Zero Trust strategy is the service connectivity layer (SCL) which abstracts the necessary network plumbing and security controls required to connect application services together regardless of location or IP address. The technology simplifies the stitching of services for developers who are not networking experts and can provide facilities such as discovery and registry, connectivity, authorization and observability. Additionally, the SCL establishes some of the foundation for Zero Trust security architectures by pushing enforcement out to the service endpoints.
## SCL Will Help Deliver Software Faster“SCL technologies (such as meshes, cloud private endpoints and service connectivity fabrics) allow developers and application architects to configure their services assuming the network is flat and that services are reachable without having to be concerned about details of the underlying network infrastructure.”
“Why this is important: SCL technologies (such as meshes, cloud private endpoints and service connectivity fabrics) allow developers and application architects to configure their services assuming the network is flat and that services are reachable without having to be concerned about details of the underlying network infrastructure,” Gartner explains. The SCL will help deliver software faster by abstracting services and connectivity between them.
Gartner also highlights that the SCL works better for organizations that have a platform operations team and have adopted infrastructure as code. Developers can concentrate more on business functionality and less on networking minutiae. Additionally, organizations that are building or operating modern distributed applications will benefit from decreased cycle time, increased productivity and operational simplicity.
The bottom line for your business according to Gartner is that, “The service connectivity layer will help deliver software faster by abstracting services and connectivity between them.” This is why Gartner classifies SCL as an Innovation Trigger due to its potential to drive advancements in Zero Trust Networking and in turn, reduce the risk of cybersecurity threats.
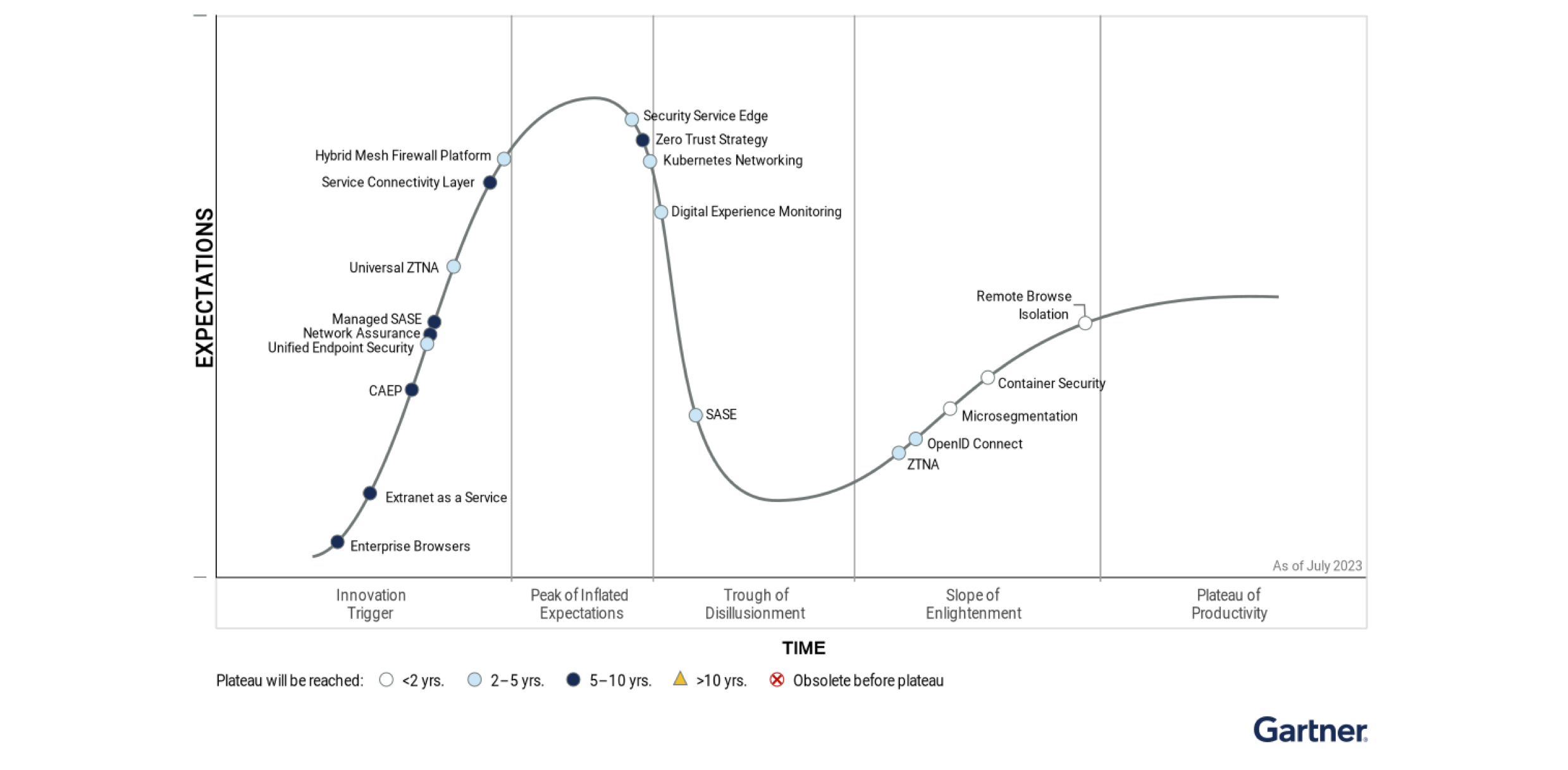

Note: This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Tetrate.
Start Your Zero Trust Journey with Tetrate
Zero Trust has huge potential for organizations to improve their security by adopting its key principles, such as bringing stronger control over access to corporate resources and ensuring that users aren’t authorized to do more than is necessary for their role. Tetrate Service Express (TSE)—Tetrate’s service mesh solution for Amazon’s EKS container service—combines Tetrate’s Istio-based service mesh solution with a Zero-trust security solution that helps users manage how their services talk to each other and outside services. Together, Tetrate and AWS deliver the fastest and easiest way to bring an Istio-based service connectivity layer and a foundation of Zero Trust to modern apps running on AWS.
Want to learn more about Tetrate’s Zero Trust solutions? Visit tetrate.io/zero-trust ›










