Zero Trust Architecture in Kubernetes
Protect your apps with end-to-end, dynamic, L7 access control
Tetrate Sets the Standards for Zero Trust Networking
Dynamic Authn/z
We use NGAC to authenticate access to your applications. It is an advanced implementation of RBAC, developed by NIST scholar David Ferraiolo.
End-to-End mTLS
Enable mTLS and prevent eavesdropping and ensure message authenticity and integrity with a click of a button across all your environments.
Trust bounded in Space & Time
Network location alone does not imply trust. Once authorized, access is granted only for a limited time and with least possible privileges.
Observable & Auditable
Integrity and security posture of all assets are continuously monitored and policy enforcement continuously assured. Insights gained from observing are fed back to improve policy.
Get Zero Trust from the People Who Set the Standards
Tetrate partners with NIST to develop standards for Zero Trust



Tetrate partners with the National Institute of Standards and Technology (NIST) to define and promote the standards for Zero Trust. NIST special publication 800-207 defines zero trust architecture. The SP 800-204, 800-204A, and 800-204B, co-authored by Tetrate offer deployment recommendations.
Tetrate Service Bridge
The only application connectivity platform with Zero Trust built-in
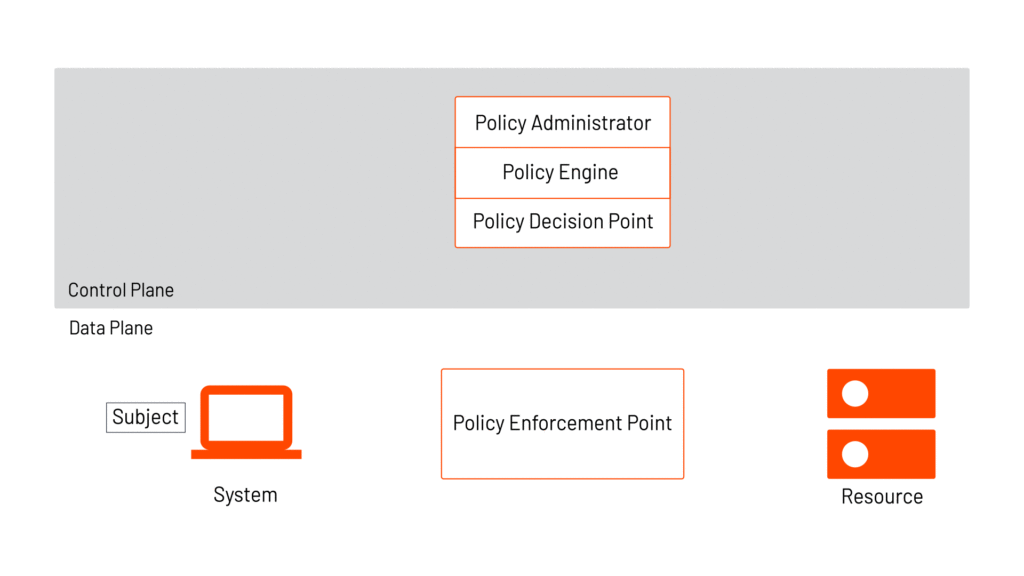
Comes preloaded with all of the controls to meet US ZTA standards, so your developers can focus on business.
App-level zoning allows for secure, fine-grained segmentation. Vetted workflows allow application, platform, and infosec teams to effectively manage policies for the entire organization. A centralized view of config changes with policy controls enables audit and continuous proof of compliance.
Connect and Secure All Your Workloads Across Environments
Integrate with your existing systems and teams
Organization Aware
Enable governance across teams with infrastructure mapping to teams, workspaces, and applications.
Ensure Policy at Runtime
Application-level segmentation with end-to-end encryption in transit plus strong end-user and workload identity, authentication and authorization.
Always Know Your Security Posture
Auditable runtime and historical proof of enforcement, plus operational awareness, including metrics, logs and traces, globally across your entire fleet