
This year’s KubeCon China marked its first-ever occurrence in Hong Kong, spanning three days. As a participant and a panel moderator, I will share in this article the highlights of the conference and the in-depth discussions on service meshes and gateway technologies.

Key Themes
This edition of KubeCon introduced a theme on AI and developers, here are some of the focal points:
- Practical Applications of Cloud Native Technologies in Industries: Especially in the electric vehicle and cybersecurity sectors, such as the joint discussion by Huawei and NIO on how cloud native technologies can accelerate innovation in electric vehicles.
- The Power of the Kubernetes Community: Detailed discussions on the influence of China’s Kubernetes community and its role in advancing regional cloud native activities.
- The Integration of Open Source Technology and Artificial Intelligence: Discussions on the advanced position of China and Hong Kong in the fields of open source and AI technologies and how these are driving regional technological innovation and development.
- Latest Developments in Service Meshes and API Gateways: Including updates on service mesh technologies and how they work in conjunction with Kubernetes schedulers to enhance system throughput.
- New Strategies for Supply Chain Security: Focusing on the latest developments in securing supply chains, particularly practical guidelines on SLSA compliance.
- Multicluster Management and Edge Computing: Discussions on strategies for effective management and innovation across different architectures and systems.
- Optimization of AI Large Model Inference Performance: Discussion on performance acceleration in serverless architectures for AI large model inference and related technological advancements.
Istio and Modern API Gateways: Exploring the Future of Service Meshes
In a roundtable discussion that I participated in with industry leaders from Tetrate, Alibaba Cloud, and Kong Inc., we delved deeply into the latest developments and integrations of Istio and API gateways.

- Innovations in Istio: We discussed the latest version update of Istio (Istio 1.123) and key features such as optimizations in the Ambient mode, a new architectural choice that reduces resource consumption while enhancing performance.
- Practical Comparison Between Ambient and Sidecar Modes:
- When to Choose Sidecar: When high isolation and detailed traffic management are required.
- When to Choose Ambient: When pursuing ultimate performance and resource efficiency.
- Challenges in the Development of Ambient Mode: Despite its advantages, Ambient mode still faces challenges in complex traffic management and multi-tenant environments.
- Service Mesh Optimization Strategies: Discussing methods to enhance the performance and efficiency of cloud applications through service mesh improvements.
- Integration of Service Meshes and API Gateways: Demonstrating how these two technologies work together to support more complex deployment and operational modes.
Future Perspectives on Istio
In the presentation by Zhonghu Xu and Jianpeng He, we gained insights into the possible future directions of Istio:
- Dual Mode Drive: Istio is likely to support both the Ambient mode and the Sidecar mode simultaneously. Ambient mode suits users seeking performance and cost optimization, while the Sidecar mode will continue to support users requiring comprehensive functionalities.
- Support for Gateway API: Istio’s support for the Gateway API provides users with more flexible routing and policy configuration options.
- Application of Waypoints Strategies: Waypoints need not be limited to Istio or Envoy. Using the Gateway API and GAMMA, any standard-compliant implementation can serve as a Waypoint, offering greater flexibility and scalability for service meshes.
Sandwich Waypoint
They emphasized the Sandwich Waypoint which represents a sophisticated approach to managing and directing traffic within Istio, especially under the Ambient Mode. This kind of waypoint proxy is designed to streamline and enhance the efficiency of traffic routing by acting as an intermediary layer that handles, transforms, and forwards traffic between clients and servers. It leverages a dual zTunnel setup where each zTunnel, situated at either end of the communication channel, collaborates to encapsulate and decode traffic. The Waypoint itself is responsible for executing additional functions such as traffic shaping, security checks, and protocol translations, thus enriching the service mesh capabilities without the overhead of sidecars. This approach allows Istio to maintain robust traffic management and security features while optimizing resource utilization and reducing latency.
It supports:
- Traffic Redirection: By setting the istio.io/use-waypoint: {namespace}/{gateway-name} annotation, traffic to a target service, pod, or within a namespace can be redirected to the same Waypoint.
- Waypoint Deployment: Users can deploy a Waypoint by creating a Gateway object. Unlike the original implementation of Waypoint, the new deployment method will include associated services and service accounts, not just the Waypoint instance.
- Routing and Policy Configuration: Using the Gateway API for routing and policy configuration provides more customization options for users and providers.
This represents a mode in Istio’s Ambient mode for capturing layer 7 traffic, as illustrated below.
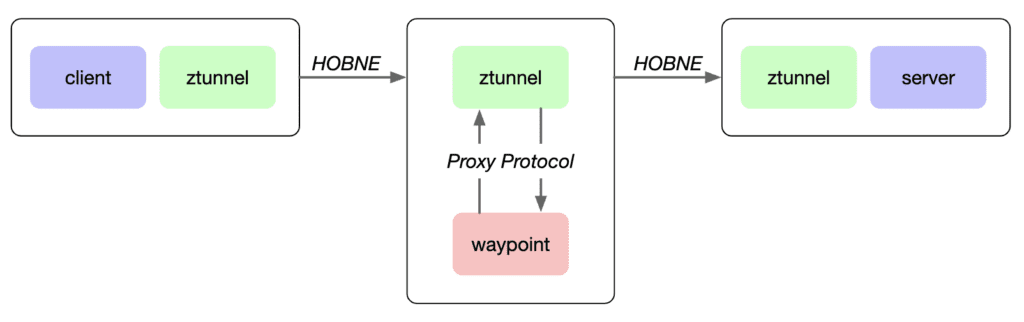
Figure 3: Sandwich Waypoint Traffic Capture
The steps for capturing layer 7 traffic with Istio Sandwich Waypoint are as follows:
- Terminate the HBONE connection via zTunnel, arriving at the Waypoint, with zTunnel responsible for decoding the HBONE protocol.
- Waypoint extracts destination addresses, source addresses, etc., to handle traffic and determine forwarding locations.
- Waypoint expands or parses the transport layer encapsulation (TLV) data, with proxies supporting TLV processing to provide additional context.
- Waypoint communicates with the peer zTunnel, coordinating with the server-side zTunnel to ensure correct traffic transfer.
- Encapsulate HBONE, sent by the server-side zTunnel to the final server destination, achieving fine-grained traffic management and routing in an Istio environment while maintaining compatibility with existing network protocols.
Cutting-Edge Extensions in Envoy Gateway
In a presentation at KubeCon, Huabing Zhao discussed how Envoy Gateway enhances its capabilities and flexibility by extending the Kubernetes Gateway API, covering a wide range of matching and routing capabilities, new resource and policy models, and details of security policies.
- Gateway API Compatibility: Envoy Gateway is fully compatible with the Gateway API and offers a wide range of matching and routing options. These include HTTP host and path matching, HTTP header-based operations, weighted load balancing, and support for gRPC, UDP, and TCP routing.
- Policies for Advanced Traffic Management: The introduction of ClientTrafficPolicy and BackendTrafficPolicy provides users with more granular control over traffic management for both upstream and downstream connections, including features such as rate limiting, retries, load balancing, circuit breakers, and more.
- Enhancement of Security and Authentication: The introduced SecurityPolicy supports CORS, HTTP basic authentication, OIDC, JWT authentication, and can integrate with various identity providers. It also provides detailed access control, allowing authorization based on the requester’s original IP, JWT claims, etc.
- Expanding Functionality with Custom Extensions: Envoy Gateway offers support for custom extensions through WASM (WebAssembly) and external process extensions. This allows users to enhance the gateway’s functionality by integrating their own customized extensions, tailored to specific use cases and operational needs.
- Future Exploration: Future versions are expected to support non-Kubernetes environments deployment, optimize memory usage in the control plane, and expand authorization capabilities.
Conclusion
Through this conference, we gained insights into Istio’s Ambient mode and the developments in Envoy Gateway. The discussions on these technologies not only forecast future trends but also provided practical insights to facilitate the implementation and innovation of technologies.