Tetrate Service Bridge
Complete, Enterprise-Grade Istio and Envoy
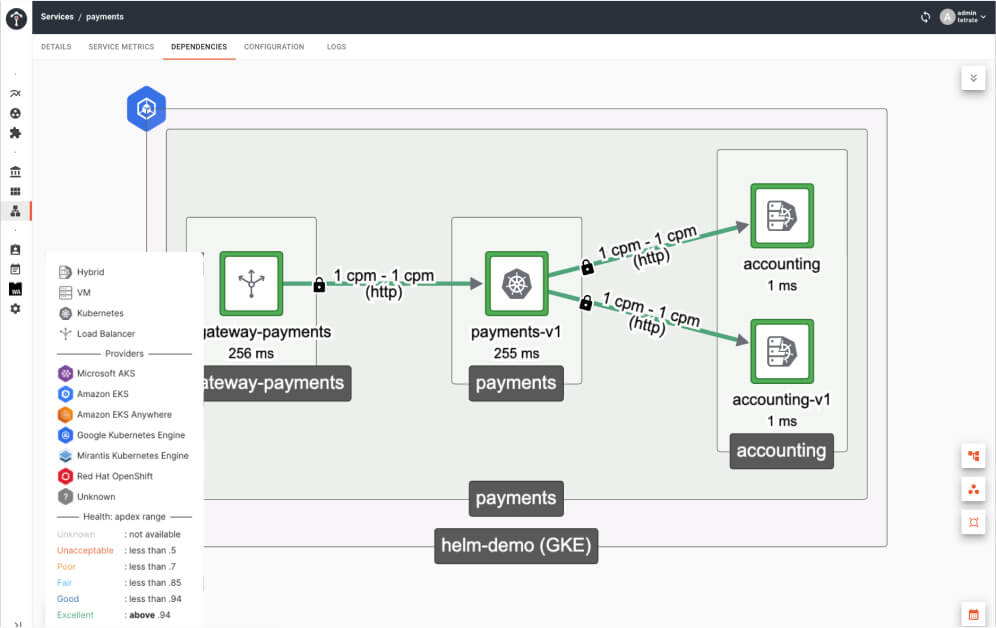
Technology and expertise come together in our industry-leading service mesh built on open source Istio and Envoy with a modern management plane that brings centralized governance and decentralized enforcement of application networking – essential for implementing a Zero Trust architecture. Tetrate Service Bridge delivers a uniform way to connect, manage, and observe microservices-based applications. It provides behavioral insight into and control of the networked microservices in your service mesh.
Tetrate Service Bridge is designed to help you maximize open source Istio and Envoy in an enterprise environment so you can:
Built For A Multi-Cloud World
Our Application Networking and Security platform supports multi-cloud environments and addresses performance across all of your cloud accounts and deployments.
Accelerate Application Delivery, Securely
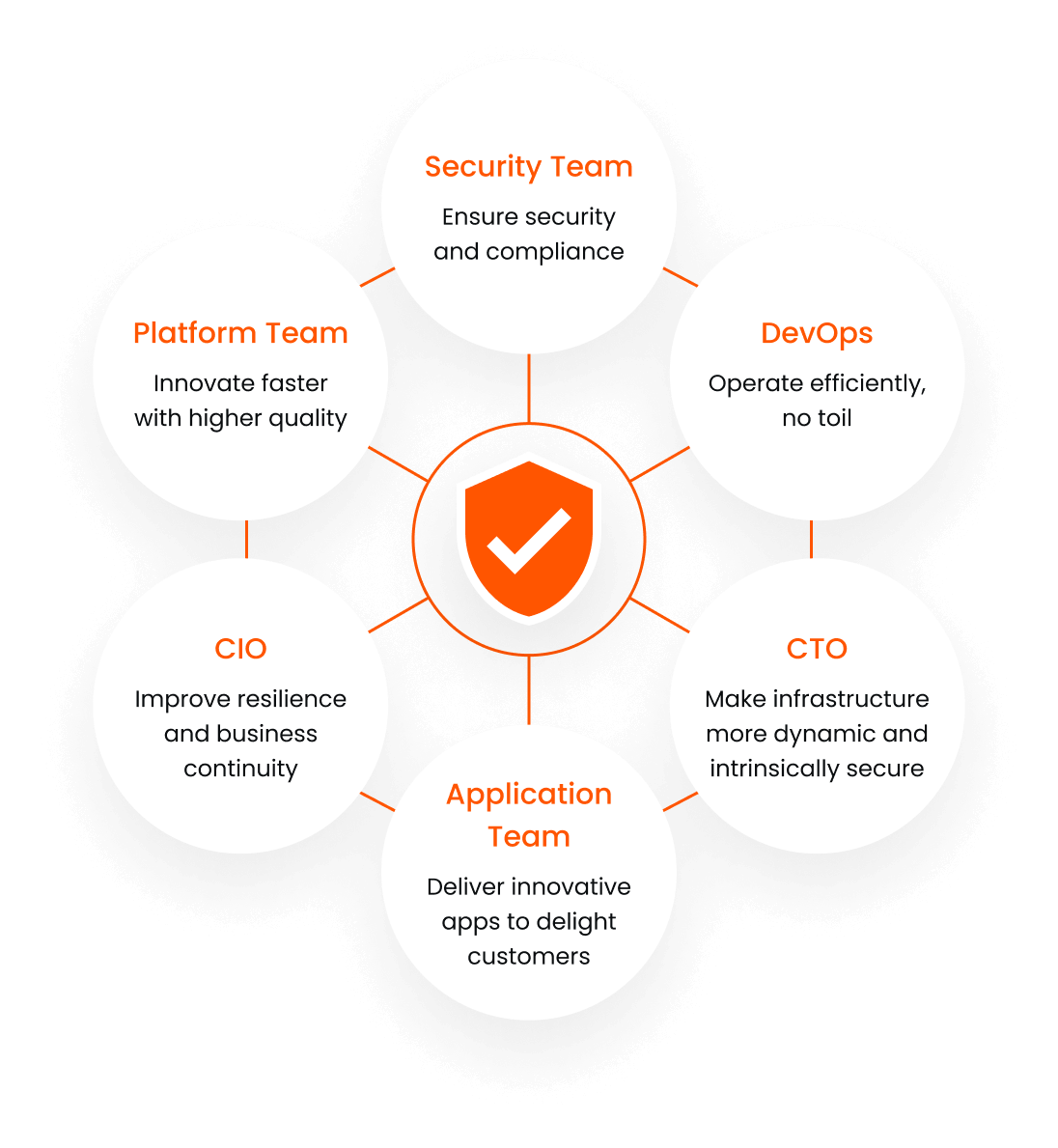
Tetrate Service Bridge is how Developer, Platform and Security teams collaborate to build modern applications faster with a foundation of Zero Trust.
Trusted By Customers And Partners
Get Enterprise-grade Support, Straight from the Creators of Istio and Envoy
Our enterprise-ready technology comes with enhanced features, 24/7 support, training architectural reviews and more. Underpinning the platform is our 99.99% uptime SLA and committer-driven expertise, providing support and services from the team with over 1M hours of technical experience with Istio, Envoy and Skywalking.
Additional Resources
Take the Next Step
Learn how we can help you scale service mesh success across your enterprise.